Setup Guidance
- Operator Checklist
- Registration Instructions
Complete each item in the checklist to ensure your node is properly configured. The checklist verifies all prerequisites are met before registration.
Access CapxCloud Operator Checklist →Stake Delegation Details
For stake delegation, the following operations should be performed: ETH to stETH:- The “submit” function on the stETH contract (address:
0x3F1c547b21f65e10480dE3ad8E19fAAC46C95034) is to be called with a value of 0.04 ETH. - The
_referralparameter should be set to0x0000000000000000000000000000000000000000.
- First, the “approve” function should be called on the stETH contract (address:
0x3F1c547b21f65e10480dE3ad8E19fAAC46C95034) with the following parameters:- spender: the wstETH contract address (
0x8d09a4502Cc8Cf1547aD300E066060D043f6982D) - amount:
40000000000000000(representing 0.04 ETH)
- spender: the wstETH contract address (
- Then, the “wrap” function should be called on the wstETH contract (address:
0x8d09a4502Cc8Cf1547aD300E066060D043f6982D) with the parameter:- _stETHAmount:
40000000000000000(representing 0.04 ETH)
- _stETHAmount:
-
Operator Opt-in for the Vault
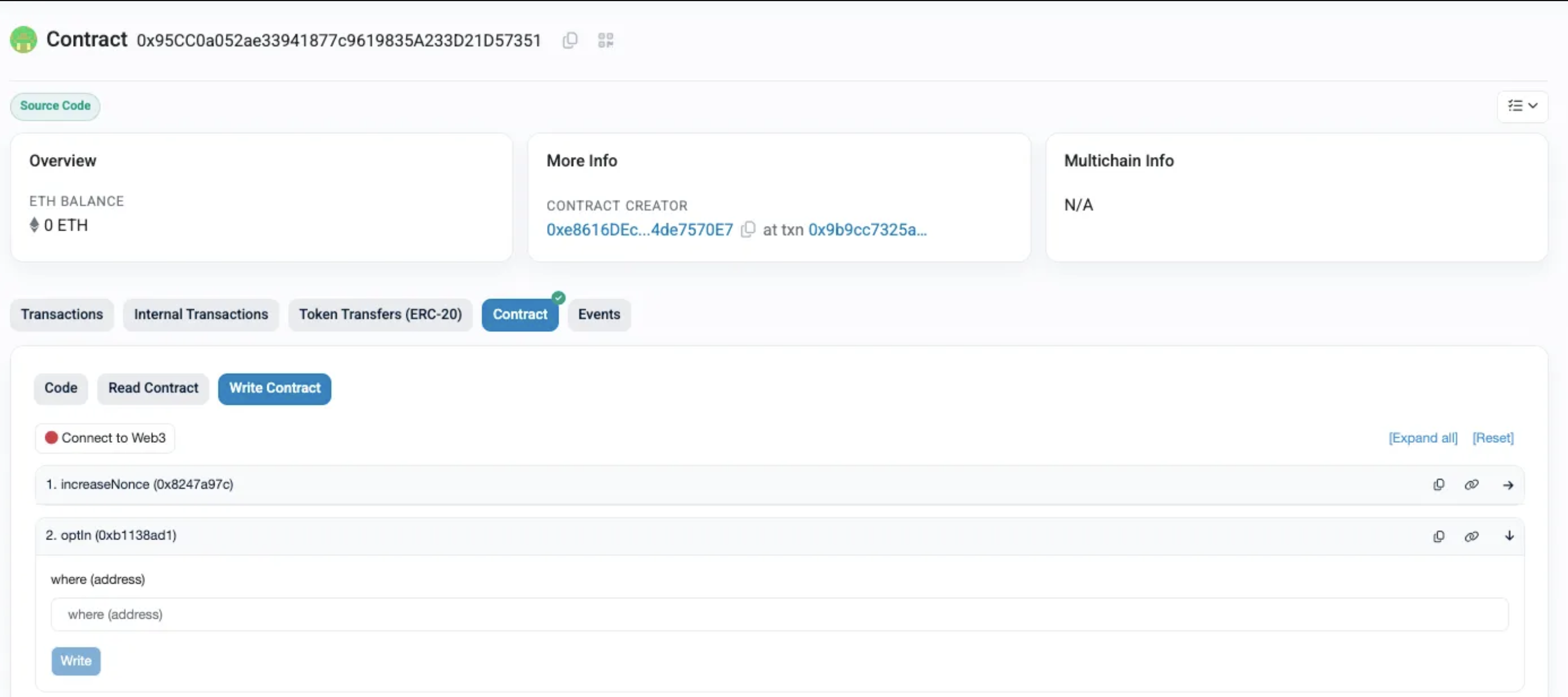
- Contract -
0x95CC0a052ae33941877c9619835A233D21D57351 - Method -
optIn ( 0xb1138ad1) - Params -
- where : the vault contract address (
0x66a95b5981461D2BA23264d4d2fe20a85199a944)
- where : the vault contract address (
- Contract -
-
First, the “approve” function should be called on the wstETH contract (address:
0x8d09a4502Cc8Cf1547aD300E066060D043f6982D) with the following parameters:- spender: the vault contract address (
0x66a95b5981461D2BA23264d4d2fe20a85199a944) - amount:
37000000000000000(representing 0.037 ETH)
- spender: the vault contract address (
-
The vault contract ( address :
0x66a95b5981461D2BA23264d4d2fe20a85199a944) requires a deposit call with two parameters:onBehalfOf: Operator address (or the address for which the deposit is made).amount: The token amount in Wei. Based on the details above, the required parameter is37000000000000000.
Wallet Configuration: Ledger/Safe vs. EOA
The appropriate environment file should be selected based on the wallet type being used.- Ledger/Safe Wallet
- EOA Wallet
Two key parameters should be configured:
-
PRIVATE_KEY_ATTESTER(Consensus Key): This parameter holds the private key that is used for consensus-related operations. It is designated as the Consensus Key and is responsible for signing messages and attestations that participate in the consensus process. -
OPERATOR_ADDRESS(Controller Key Address): This parameter holds the wallet address associated with the controller key. It is used to manage administrative functions and operator configurations. The separation of these keys helps enhance security by ensuring that the key used for consensus operations is distinct from the one controlling operator privileges.
Operator ( Attestor Node ) Setup
Key Features
- Basic P2P attestation node implementation
- Network discovery and peer connection
- Integration with Symbiotic protocol security layer
- Attestation service foundations
- Minimal operator configuration requirements
Docker Images
Attester P2P Node (Testnet)
Validation Service (Testnet)
Docker Compose file
Instructions for Running the Setup
- Prerequisites:
- It is expected that Docker and Docker Compose are installed.
- Ensure that the required environment variables are configured either in a
.envfile or in your shell environment.
- Deploying the Services:
- Navigate to the directory containing the Docker Compose file.
-
Execute the following command to start the services in detached mode:
- The services will be initiated in the background.
- Monitoring Logs:
-
To monitor the logs for all services in real time, it is advised to use:
- This command will stream the logs continuously, allowing for live troubleshooting.
-
To monitor the logs for all services in real time, it is advised to use:
- Managing the Deployment:
-
To stop the services, the following command can be used:
-
If an update of the images is needed, it is recommended to run:
-
To stop the services, the following command can be used:
